Researchers at GW have developed a novel solution that serves to capture the activity of an adversary in a cache timing channel. The novel solution can detect advanced attack variants of cache timing channel which can evade the detection of the existing technology by mimicking activities of benign applications and obfuscating mutual eviction patterns. The novel solution can also mitigate efficiently detected cache timing channels by re-purposing existing hardware prefetcher. The novel solution utilizes cache reuse distance, in that it measures cache reuse distance to captures the necessary activity of a spy or an adversary in every cache timing channel variant.
The disclosed invention can be implemented as either an apparatus, a device, a system, or a method as can be appreciated. The disclosed invention can include various aspects as follows: (i) a recording module that can measure and record a cache reuse distance associated with a computing application or aspect and which aspect can include a cache timing channel; (ii) an identification module that can identify an adversary attempting to utilize various advanced attack variants of cache timing channels as can be appreciated; (iii) at least one mitigating module that can mitigate any illegal communication that may transpire in a given cache timing channel. The researchers were able to achieve a significant bit error rate for an adversary based on conducted experiments.
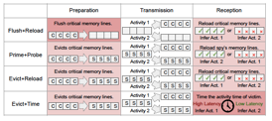
Fig. 1 – One example of an aspect of the disclosed invention
Applications:
- Cybersecurity applications in various fields
- Through detection of advanced variants of cache timing channels
Advantages:
- Ability to detect advanced attack variants of cache timing channel which can evade the detection of the existing technology by mimicking activities of benign applications and obfuscating mutual eviction patterns
- Ability to mitigate efficiently detected cache timing channels by re-purposing existing hardware prefetcher